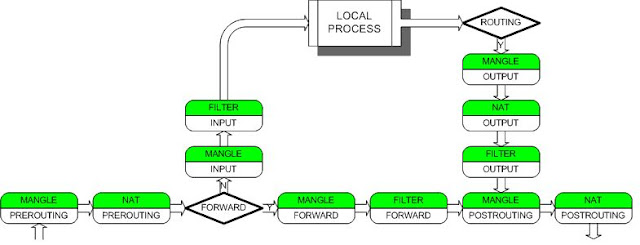
#iptable structure is: iptables -> Tables -> Chains -> Rules.

#http://www.thegeekstuff.com/2011/01/iptables-fundamentals
#iptables -t nat --list --> show all the available firewall rules, if you don’t specify the -t option, it will display the default filter table.
vim iptables.sh
#!/bin/bash
#enable ip forwarding
echo 1 > /proc/sys/net/ipv4/ip_forward
IPT='/sbin/iptables'
#clear iptables
#-t, --table is tables store in /proc/net/ip_tables_names (default is nat and filter only)
#-F, --flush is deleting all the rules one by one
#-X, --delete-chain is delete the optional user-defined chain specified.
#-P, --policy is set the policy for the chain to the given chain target (eg. PREROUTING).
#nat table only got 3 predefinded chains (PREROUTING, POSTROUTING, OUTPUT)
#filter table only got 3 predefinded chains (INPUT, FORWARD, OUTPUT)
#ACCEPT – Firewall will accept the packet.
#DROP – Firewall will drop the packet.
for a in `cat /proc/net/ip_tables_names`; do
${IPT} -F -t $a
${IPT} -X -t $a
if [ $a = nat ]; then
${IPT} -t nat -P PREROUTING ACCEPT
${IPT} -t nat -P POSTROUTING ACCEPT
${IPT} -t nat -P OUTPUT ACCEPT
elif [ $a = mangle ]; then
${IPT} -t mangle -P PREROUTING ACCEPT
${IPT} -t mangle -P INPUT ACCEPT
${IPT} -t mangle -P FORWARD ACCEPT
${IPT} -t mangle -P OUTPUT ACCEPT
${IPT} -t mangle -P POSTROUTING ACCEPT
elif [ $a = filter ]; then
${IPT} -t filter -P INPUT ACCEPT
${IPT} -t filter -P FORWARD ACCEPT
${IPT} -t filter -P OUTPUT ACCEPT
fi
done
WAN="eth0"
LAN="eth1"
#-A,
--append is append one or more rules to the end of the selected chain.
#-o, --out-interface is name of an interface via which a packet is going to be sent.
#-j, --jump is specifies the target of the rule; i.e., what to do if the packet matches it. eg. ACCEPT, REJECT, DNAT (Destination NAT)
#MASQUERADE target is specified to mask the private IP address of a node with the external IP address of the firewall/gateway. (源地址伪装。它可以实现自动寻找到外网地址,而自动将其改为正确的外网地址。).eg. unifi router gateway, act as router or gateway. eg2. eth0 = internet and masquerade it, eth1 is 10.0.1.0 network range, without masquerading, anybody connects to the eth0 wont be able to route to the other range.
${IPT} -t nat -A POSTROUTING -o $WAN -j MASQUERADE
${IPT} -t nat -A POSTROUTING -o $LAN -j MASQUERADE
#Remote Desktop
#-i, --in-interface is name of an interface via which a packet was received.
#-d, --destination is destination specification.
#-p, --protocol is tcp, udp, icmp, icmpv6, etc.
#--dport is the destination port.
#DNAT is destination NAT.
#-m, --match is specifies a match to use.
#--state eg. 只允许状态为NEW的进来 (** 对于整个TCP协议来讲,它是一个有连接的协议,三次握手中,第一次握手,我们就叫NEW连接,而从第二次握手以后的,ack都为1,这是正常的数据传输,和tcp的第二次第三次握手,叫做已建立的连接(ESTABLISHED).
${IPT} -t nat -A PREROUTING -i $WAN -d <debian_internal_ip> -p tcp --dport 3389 -j DNAT --to <windows_internal_ip>:3389
${IPT} -A INPUT -i $WAN -d <debian_internal_ip> -p tcp --dport 3389 -j ACCEPT
${IPT} -A FORWARD -i $WAN -p tcp --dport 3389 -m state --state NEW -j ACCEPT
#Only below rules is also OK:
#iptables -t nat -A PREROUTING -p tcp --dport 3389 -j DNAT --to-destination win-box:3389
#iptables -A FORWARD -p tcp --dport 3389 -j ACCEPT